Off the Top: Privacy Entries
Showing posts: 1-5 of 5 total posts
Selective Sociality and Social Villages
The web provides wonderful serendipity on many fronts, but in this case it brought together two ideas I have been thinking about, working around, and writing about quite a bit lately. The ideas intersect at the junction of the pattern of building social bonds with people and comfort of know interactions that selective sociality brings.
The piece that struck me regarding building and identifying a common bond with another person came out of Robert Paterson's "Mystery of Attraction" post (it is a real gem). Robert describes his introduction and phases of getting to know and appreciate Luis Suarez (who I am a huge fan of and deeply appreciate the conversations I have with him). What Robert lays out in his introduction (through a common friend on-line) is a following of each other's posts and digital trail that is shared out with others. This builds an understanding of each others reputation in their own minds and the shared interest. Upon this listening to the other and joint following they built a relationship of friendship and mutual appreciation (it is not always mutual) and they began to converse and realized they had a lot more in common.
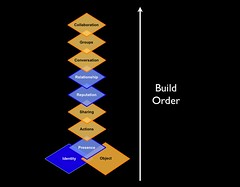 What Robert echos is the Elements in Social Software and its build order. This build order is common in human relationships, but quite often social software leaves out steps or expects conversations, groups, and collaboration to happen with out accounting for the human elements needed to get to this stage. Quite often the interest, ideas, and object (all social objects) are the stimulus for social interaction as they are the hooks that connect us. This is what makes the web so valuable as it brings together those who are near in thought and provides a means to connect, share, and listen to each other. I really like Robert's analogy of the web being like university.
What Robert echos is the Elements in Social Software and its build order. This build order is common in human relationships, but quite often social software leaves out steps or expects conversations, groups, and collaboration to happen with out accounting for the human elements needed to get to this stage. Quite often the interest, ideas, and object (all social objects) are the stimulus for social interaction as they are the hooks that connect us. This is what makes the web so valuable as it brings together those who are near in thought and provides a means to connect, share, and listen to each other. I really like Robert's analogy of the web being like university.
Selective Sociality of Villages
The piece that resonated along similar threads to Robert's post is Susan Mernit's "Twitter & Friend Feed: The Pleasure of Permissions". Susan's post brings to light the value of knowing who you are sharing information with and likes the private or permission-based options that both Twitter and FriendFeed offer. This selective sociality as known Local InfoCloud of people and resources that are trusted and known, which we use as resources. In this case it is not only those with whom we listen to and query, but those with whom we share. This knowing who somebody is (to some degree) adds comfort, which is very much like Robert Patterson and Luis Suarez#039; villages where people know each other and there is a lot of transparency. Having pockets where our social armor is down and we can be free to share and participate in our lives with others we know and are familiar to us is valuable.
I am found these two pieces quite comforting as they reflect much of what I see in the physical community around me as well as the work environments I interact with of clients and collaborators. The one social web service I have kept rather private is Twitter and I really want to know who someone is before I will accept them as a connection. This has given me much freedom to share silly (down right stupid - in a humorous way) observations and statements. This is something I hear from other adults around kids playgrounds and practices of having more select social interactions on line in the services and really wanting to connect with people whom they share interests and most often have known (or followed/listened to) for sometime before formally connecting. Most often these people want to connect with the same people on various services they are trying out, based on recommendation (and often are leaving a service as their friends are no longer there or the service does not meet their needs) of people whom they trust. This is the core of the masses who have access and are not early adopters, but have some comfort with the web and computers and likely make up 80 to 90 percent of web users.
[Comments are open (with moderation as always) on this post at Selective Sociality and Social Villages :: Personal InfoCloud]
DataPortability Video is Place to Start Understanding
Marchall Kirkpatrick at ReadWriteWeb has posted a good background about New Video Explains the Basics of Data Portability. The DataPortability - Connect, Control, Share, Remix video is under 2 minutes in length and explains the reasons why the DataPoratbility.org group is important. It aims to ease the pain many are experiencing as they use more social media, social web services, social networks, and/or social computing services in their personal and work life.
Control
The biggest piece in this for me is control with translates to services respecting privacy wishes among other desires around trust and control of sharing. As Tom Raftery points out With the rising interest in, and use of Social Networks (FaceBook, Plaxo et al) there is growing unease in what those sites are doing with your data, never mind the inconvenience of uploading all your data every time you join a new site. The DataPortability.org aims to include in its focus data that is "shared between our chosen (and trusted) tools and vendors".
I have been working around the edges on a project whose aim is to respect these privacy wishes. This is one of the things that really needs to be at the core of all services entering into this market segment.
Ghosts of Technology Past, Present, and Future
The past two days have brought back many memories that have reminded me of the advances in technology as well as the reliance on technology.
Ghost of Rich Web Past
I watched a walk through of a dynamic prototype yesterday that echoed this I was doing in 1999 and 2000. Well, not exactly doing as the then heavy JavaScript would blow up browsers. The DHTML and web interfaces that helped the person using the site to have a better experience quite often caused the browser to lock-up, close with no warning, or lock-up the machine. This was less than 100kb of JavaScript, but many machines more than two years old at that time and with browsers older than a year or two old did not have the power. The processing power was not there, the RAM was not there, the graphics cards were not powerful, and the browsers in need of optimizing.
The demonstration yesterday showed concepts that were nearly the exact concept from my past, but with a really nice interface (one that was not even possible in 1999 or 2000). I was ecstatic with the interface and the excellent job done on the prototype. I realized once again of the technical advances that make rich web interfaces of "Web 2.0" (for lack of a better term) possible. I have seen little new in the world of Ajax or rich interfaces that was not attempted in 2000 or 2001, but now they are viable as many people's machines can now drive this beauties.
I am also reminded of the past technologies as that is what I am running today. All I have at my beck and call is two 667MHz machines. One is an Apple TiBook (with 1 GB of RAM) and one is a Windows machine (killer graphics card with 256MB video RAM and 500MB memory). Both have problems with Amazon and Twitter with their rich interfaces. The sites are really slow and eat many of the relatively few resources I have at my disposal. My browsers are not blowing up, but it feels like they could.
Ghost of Technology Present
The past year or two I have been using my laptop as my outboard memory. More and more I am learning to trust my devices to remind me and keep track of complex projects across many contexts. Once things are in a system I trust they are mostly out of my head.
This experience came to a big bump two days ago when my hard drive crashed. The iterative back-ups were corrupted or faulty (mostly due to a permission issue that would alter me in the middle of the night). The full back-up was delayed as I do not travel with an external drive to do my regular back-ups. My regularly scheduled back-ups seem to trigger when I am on travel. I am now about 2.5 months out from my last good full back-up. I found an e-mail back-up that functioned from about 3 weeks after that last full backup. Ironically, I was in the midst of cleaning up my e-mail for back-up, which is the first step to my major back-up, when the failure happened.
I have a lot of business work that is sitting in the middle of that pile. I also have a lot of new contacts and tasks in the middle of that period. I have my client work saved out, but agreements and new pitches are in the mire of limbo.
Many people are trying to sync and back-up their lives on a regular basis, but the technology is still faulty. So many people have faulty syncing, no matter what technologies they are using. Most people have more than two devices in their life (work and home computer, smart phone, PDA, mobile phone with syncable address book and calendar, iPod, and other assorted options) and the syncing still works best (often passably) between two devices. Now when we start including web services things get really messy as people try to work on-line and off-line across their devices. The technology has not caught up as most devices are marketed and built to solve a problem between two devices and area of information need. The solutions are short sighted.
Ghost of the Technosocial Future
Last week I attended the University of North Carolina Social Software Symposium (UNC SSS) and while much of the conversation was around social software (including tagging/folksonomy) the discussion of technology use crept in. The topic of digital identity was around the edges. The topic of trust, both in people and technology was in the air. These are very important concepts (technology use, digital identity, and trusted technology and trusted people). There is an intersection of the technosocial where people communicate with their devices and through their devices. The technology layer must be understood as to the impact is has on communication. Communication mediated by any technology requires an understanding of how much of the pure signal of communication is lost and warped (it can be modified in a positive manner too when there are disabilities involved).
Our digital communications are improving when we understand the limitations and the capabilities of the technologies involved (be it a web browser of many varied options or mobile phone, etc.). Learning the capabilities of these trusted devices and understanding that they know us and they hold our lives together for us and protect our stuff from peering eyes of others. These trusted devices communicate and share with other trusted devices as well as our trusted services and the people in our lives we trust.
Seeing OpenID in action and work well gave me hope we are getting close on some of these fronts (more on this in another post). Seeing some of the great brains thinking and talking about social software was quite refreshing as well. The ability to build solid systems that augment our lives and bring those near in thought just one click away is here. It is even better than before with the potential for easier interaction, collaboration, and honing of ideas at our doorstep. The ability to build an interface across data sets (stuff I was working on in 1999 that shortened the 3 months to get data on your desk to minutes, even after running analytics and working with a GIS interface) can be done in hours where getting access to the wide variety of information took weeks and months in the past. Getting access to data in our devices to provide location information with those we trust (those we did not trust have had this info for some time and now we can take that back) enables many new services to work on our behalf while protecting our wishes for whom we would like the information shared with. Having trusted devices working together helps heal the fractures in our data losses, while keeping it safe from those we do not wish to have access. The secure transmission of our data between our trusted devices and securely shared with those we trust is quickly arriving.
I am hoping the next time I have a fatal hard drive crash it is not noticeable and the data loss is self-healed by pulling things back together from resources I have trust (well placed trust that is verifiable - hopefully). This is the Personal InfoCloud and its dealing with a Local InfoCloud all securely built with trusted components.
Odd Moments in the Day - Odd Moments with Technology?
Today brought an odd moment. I looked up at iChat (my IM interface) and I see my name (Thomas Vander Wal) and podcast under Jeremy's name, which means Jeremy is most likely listening to a podcast interview with me. I had never seen that before.
Now I decide to share that odd moment with Jeremy, which I did not realize would cause Jeremy to have an odd moment.
How can the world of pervasive/ubiquitous computing ever get off the ground when we give each other odd moments through our friendly stalking? By the way I prefer using stalking, where as some people like the term monitoring, but the term monitoring does not cause me to think about privacy implications that I believe we must resolve within ourself or learn to better protect our privacy.
The incident today still causes me to chuckle for a short moment then realize how open we are with things on the internet and how different that seems to be even though most of our life has been public, but to a smaller and more localized group. It also resignals that change that came with the internet (well and much of technology) is that we can not see those who can see us. In a town we know the local video store guy knows what we rent, but now Amazon knows what we bought as do those people on our friends list whom we share our purchases with so they can have some insight as what to buy. My local video store guy in San Francisco, near California and 2nd or 3rd Avenue, was amazing. He knew everything I rented in the last few months and would provide perfect recommendations. Did he use a computer to aid himself? Nope, he was just that good and his brain could keep the connection between a face and videos rented and if you liked that video. He knew my taste perfectly and was dead on with recommendations. Not only was he on with me, but most others who frequented his store. He was great recommending, but also could help people avoid movies they did not like.
Was the guy in the video store freaky? Not really, well to me. He was a person and that was his role and his job. I worked in a coffee house for a while first thing in the morning. After a couple months I knew who the first 10 customers would be and I knew about half of the orders or possible variations of what people would order. People are patterned, I could tie the person's face to that pattern for espresso coffee drink order and I could recommend something that they should try. To some this was a little disturbing, but to most is was endearing and was a bond between customer and shopkeeper as I cared enough to know what they would like and remembered them (I did not often remember their names and most of them I did not know their names), but I knew what they drank. If is the familiarity.
So, with technology as an intermediary or as the memory tool what is so freaky? Is it not seeing into somebody's eyes? Is it the magic or somebody more than 3,000 miles away knowing what you are listening to and then have the person whom you are listening to pop-up for a chat? I think it is we have collapsed space and human norms. It is also difficult to judge intent with out seeing face or eyes. I was in a back and forth recently with a friend, but could not sense their intent as it seemed like the tone was harsh (for a person whom I trust quite a bit and think of as being intensely kind and giving) and I finally had to write and ask, but it was written from a point where I was bothered by the tone. My problem was I could not see the eyes of the person and see they playfulness or gestures to know their intent was playful challenging.
While at the Information Architecture Summit a couple/few weeks ago in Vancouver a few of us went to dinner and we played werewolf (my first time playing). But, I was reminded that the eyes hold a lot of information and carry a lot of weight in non-verbal communication. I could pick the werewolf whose eyes I could see, but in two occasions the werewolf was sitting next to me and I could not see their eyes. There was one person in each of the two games whom I did think was the werewolf as their eyes were signaling similarly to people who were not telling the truth in the cultures I grew up in.
Could technology be more easily embraced if it had eyes? Should we have glancing as Matt Webb has suggested and built an application to suggest? But could we take Matt'a concept farther? Would it be helpful?
This was a long post of what was just going to be pointing out an odd moment in the day.
Microsoft and the DOJ Data Search Request
Yesterday at the Microsoft Search Champs v4 Microsoft peeled back the layers around their dealings with providing the U.S. Government with data around search. Joshua Porter writes-up U.S. Government request and Microsoft responce. The Microsoft discussion was very open and but was closed to those of us in the room. Late in the day we were told we could openly blog the information and discuss it.
A few of us got together last night to discuss the information and recorded the discussion in a podcast the privacy and Microsoft response to DOJ (MP3 10mb 42 minutes hosted on Alex Barnett server). The podcast is a discussion between:
- Joshua Porter (Search Champs Attendee )
- Chris Pirillo ( Search Champs Attendee )
- Dion Hinchcliffe ( Search Champs Attendee )
- Fred Oliviera ( Search Champs Attendee )
- Alex Barnett ( Microsoft )
- Brady Forrest ( MSN Search Team )
- Myself, Thomas Vander Wal ( Search Champs Attendee )
Robert Scoble was the first to break the news in his blog.
From my personal perspective it was very refreshing to hear Microsoft be open with their thoughts and openly admitting they may have dropped the ball, not in the data they gave (because the data given was not personal data in any shape or form). They openly admitted they need to be a more open citizen of the internet. They have responsibility to be open with the personal information and data, which we as citizens of the web trust those with our digital tracks. There is a compact between the people using tools and the providers of internet tools that our digital rights are protected.
I have a very strong belief that Microsoft is a good citizen that looks out for my privacy. This was a trust I did not think I would have at any point in my life. It is a trust today that I have with them, but it will be a trust they must continue to foster. There are many in the Search Champs that strongly believe all of the search and portal companies must work together to ensure they are consistent in protecting the privacy of the digital citizens that interact with them. There was a lot of Google love that was lost with their public spin to try and drive a wedge between themselves and the other search engines and portals. Google was very good in publicly pointing out the DOJ request and getting public attention on the request. But, Google must work together with Yahoo!, Microsoft, AOL to protect not only digital citizens but their whole industry.